


The health and safety of your family depend on your freezer. You have a problem if the food in your freezer is not completely frozen. Likewise,...



If you are one of those who are looking for information about what is gte technology then this article is for you. Here were collected main...


Today the world is rapidly developing. Some new things that help people in one way or another, bring new emotions or just pleasantly surprise them regularly...


There are a lot of different factors to consider when purchasing a laptop. You need to find the right one that meets your specific needs. If...



What is penetration testing? Penetration testing or “pen test” for short is a tool to manage computer system vulnerability. The computer system has been under attack...



For long businesses have used spreadsheets as their usual tool for expense management data entry. Though it seems reasonable to consider that excel spreadsheet are a...


A well-crafted review of cloud applications is a must for every business. The review should be written in an engaging and interesting way that will keep...



Testing and monitoring networks regularly is a viable way to identify and fix vulnerabilities. In addition, vulnerability management programs help to recognize these vulnerabilities and fix...
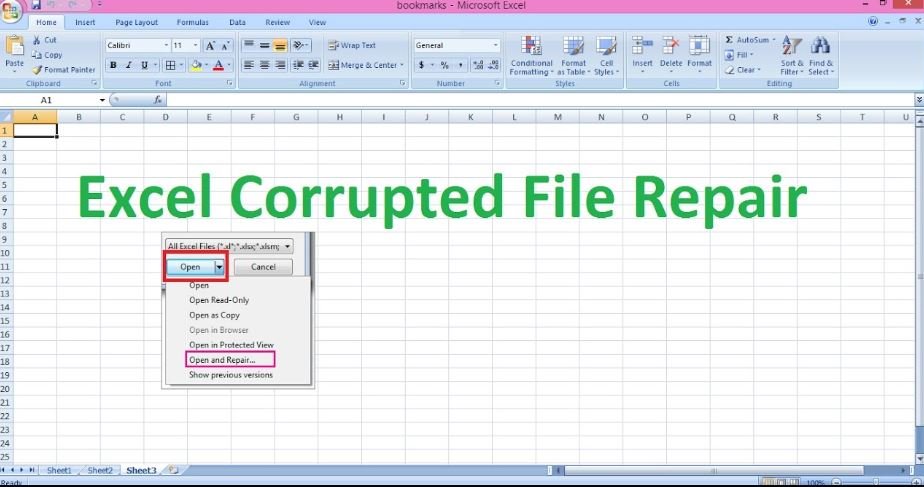
Excel files are some of the most commonly used files in the world. They store important data, and when they are corrupted, it can be a...



In 2022, many people assume faxing has gone by the wayside. While it’s true that there are far fewer fax machines now than there were before...