Apps
Complete HIPAA Compliance Checklist for In-App Chat Development 2021
HIPAA, abbreviated for Health Insurance Portability and Accountability Act, released in 1996, is a US Federal law that represents protecting and keeping patients’ private medical records and personal health information confidential in any form. This law determines the means of storing and sharing Protected Health Information (PHI) over technology, including apps.
Every organization associated with healthcare must implement all possible measures to meet the compliance requirements. Hence, before starting the mobile app or software development, development companies need to understand the HIPAA compliance requirement checklists.
[lwptoc]
HIPAA Checklist – Terminologies and Rules
Non-compliance with the demands of the act may lead to severe punishment for both companies and individuals responsible for it. Henceforth, all companies spend a tremendous amount of time in HIPAA compliant chat api development before releasing the final product.
Let’s start with the associated legal HIPAA terminologies:
-
Protected Health Information in HIPAA:
Primary purpose of HIPAA is to protect the Protected Health Information. PHI is collective data related to the patients, including their details such as addresses, contact numbers, social security numbers, account and certificate numbers, and biometric identities.
-
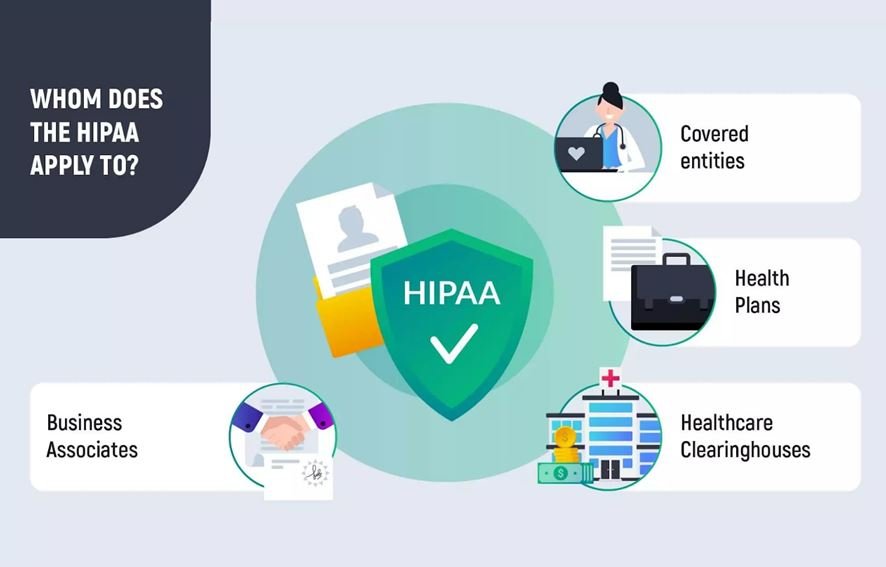
Covered Entities in HIPAA Act
Covered Entities (CE) are the:
- Health plans – insurance and health maintenance companies
- Health care clearinghouses – organizations, associated with PHI
- Health care providers – includes hospitals and medical services
Who access, transmit electronically any health information related to the transactions under which the Department of Health and Human Service has incorporated the standards.
-
Business Associates in HIPAA Act
All those who are not directly involved in the medical field yet collect, store, maintain or transmit the PHI on behalf of the covered entities referred to as business associates. More often Software Developers, and professionals like lawyers, auditors fall under this category.
Thus, a HIPAA Compliance Checklist for IT is compulsory for any healthcare software development.
HIPAA Compliance Rules- the best practices for an in-app Chat Development
Electronic PHI is advantageous with easy mobility, usability, and efficiency, compared to the traditional paper-based methods. However, the same electronic data poses a threat of data breach. Hackers may steal and sell essential data or chances of random unauthorized access and modifications of medical records. In all these cases, there will be substantial personal damage to the patients.
The five significant rules enforced to all companies for HIPAA compliance application development are as follows:
-
Privacy Rule of HIPAA
HIPAA privacy rule denotes the checklists concerned with PHI protection, focusing on protecting clinical history, diagnosis, medical record, payment details for healthcare, and other such information and strictly unavailable for third parties.
The rule denotes the specific conditions under which the PHI can be accessible without the patient’s authorization.
-
Security Rule of HIPAA
HIPAA security rules compliance signifies the requirements of the PHI security, consisting of specific recommendations and limitations in healthcare information, thus, allowing to detection, correct, and prevent future security threats.
As per this rule, all the covered entities must conduct a systematic data breach analysis to ensure authentic PHI protection.
-
Enforcement Rule of HIPAA
Enforcement Rule covers the investigation provisions and the specific penalties in case of a data breach.
The penalty amount depends on the number of medical data exposed and the frequency of data breaches in an organization starting from $100 -$50,000 for the first time.
-
Breach Notification Rule of HIPAA
Breach Notification Rule denotes notifying all the affected individuals, in case of a data breach involving individuals below 500 within 60 days of occurrence and the Department of Health and Human Services’ office for Civil Rights of such issues within 60 days of the start of a new calendar year.
Upon exceeding 500+ data breaches, the particular organization must notify the media.
-
Omnibus Rule of HIPAA
Omnibus Rule 2013 supplements all the rules mentioned above.
Furthermore, this rule expands the obligations of healthcare professionals, physicians with regards to HIPAA protection and impacts the business associates the most.
Read more: What to Learn from Other App Failures
Guide to HIPAA Compliance for an in-app Chat Development
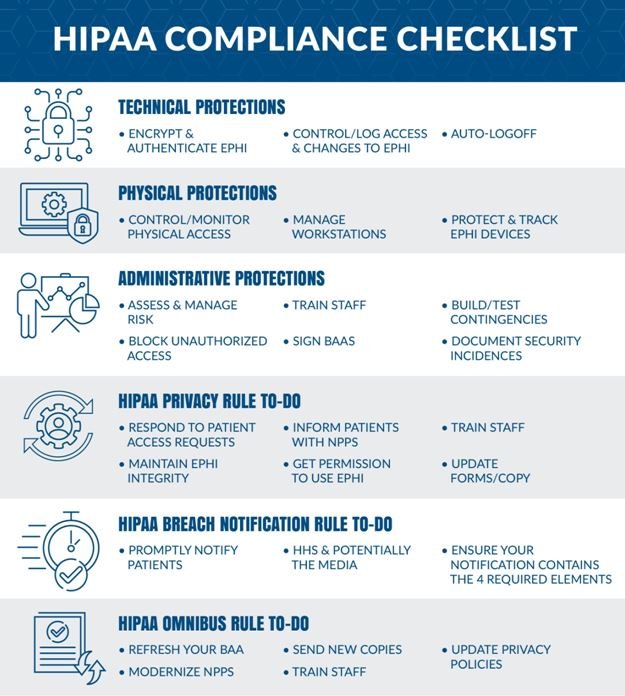
Developing a software application for healthcare providers is challenging. HIPAA Software Security rules denote specific precautionary requirements critical to follow for any healthcare app development purpose. The following section briefs you on the HIPAA Compliance Checklist for Software Development.
-
The User Authorization
The U.S. government diverges the quality of identity assurance into four levels, starting with the lowest to very high confidence in the asserted identity. The lowest levels require only a single-factor authentication like a password. A multi-factor authentication such as approved mobile number, email ids, location, etc., is necessary for the higher levels except for doctors.
While building HIPAA Compliant Software, companies need to include at least two of these following factors.
- Knowledge: Visitors must provide unique data like PIN and Passwords that only a legit user knows.
- Possession: The platforms provide users with additional unique information like security code, where the visitor must enter data to prove legitimate access.
- Inherence: Visitors need to verify inherent characteristics such as a biometric scan or facial recognition.
- Location: A user must be in a particular place at the time of access.
-
The Remediation Plan
A remediation plan comprises various measures considered by organizations that describe their best practices, distinguishing responsibilities. A HIPAA-compliant application plan must describe the following aspects of an organization’s security:
- List of main tasks for ultimately securing data.
- List of members and their tasks with responsibilities.
- List of plans, action documents to overcome hurdles in the future.
-
The Emergency Mode
An emergency mode plan is a cumulative list of activities that an organization will proceed with during an attack, and its HIPAA compliance Security Checklist must have:
- List of all team members with roles, contact info, and responsibilities directly connected to data security assurance.
- Description of all digital healthcare systems.
- Recovery, Procedure plan, and emergency facilities for informing staff and patients.
-
The Authorization Monitoring
According to HIPAA compliance requirements, organizations must monitor the efficiency and safety of access algorithms at a regular time. Healthcare IT teams can increase their data access algorithm by:
- Activity logs and controls: Record activity logs and interactions with all users’ systems and notify any suspicious attempts to access the server infrastructure.
- Auto log-offs: If the user forgets to log off, the system must log out the user when the shifts are over.
- Access control for emergency cases: The organization must provide access to the user’s profile during emergencies, even when the user isn’t physically present in the office.
-
The Data Backup
HIPAA security software rule emphasizes that all EPHI must be duplicated on another dependable data storage, including backup of patient’s data and all media files periodically.
Organizations need to adhere to the following key aspects:
- Redundancy: You should have three copies of data and store two copies with independent access.
- Encryption: Must encrypt all data with 256-bit AES protocol, secured with two-way authentication.
- Transfers: While data transfer into a cloud provider or public servers, it must be 256-bit encrypted and undecipherable.
- Monitoring: Restoring lost data with the original, and the system should alert the organization at any backup failure.
The HIPAA Compliance Certification for Software
The governing body for HIPAA compliance is the Office of Civil Rights(OCR) and comes under the US’s Department of Health and Human Services. Neither they neither provide nor endorse any organization with any such certification provision.
Thus, there is no HIPAA compliance certificate for the software. Hence, it would be best if you adopted the complete HIPAA compliance software checklist.
Create Your Apps with HIPAA Compliance
Implementation of all the rules required by HIPAA is time-consuming and challenging. Still, those requirements protect healthcare companies from data breaches and save them from severe penalties.
Furthermore, it takes years of experience to develop HIPAA Compliant apps with vital testing, retesting the security measures, and building a less risky app environment.
Read more: Live Video Call APIs & SDKs to be considered for your Android, iOS & Web Apps












